Inroduction to PKI Models
There are two commonly used PKI models :
- Hierarchical PKI
- Bridge PKI
Hierarchical PKI
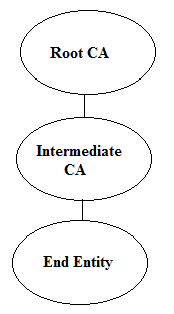
In this simple hierarchical PKI, there is one self signed Root CA certificate. Self signed Root CA certificate signs itself with its own private key. Root CA is normally a trust anchor for the applications that process the certificates. If the Root CA is not trusted locally in different applications then any certificate issued under the Root CA hierarchy should not be trusted.
There are applications that already have list of trusted Root CAs bundled. The certificates that are under the hierarchy of any of the bundled Root CAs is automatically trusted e.g. internet browsers ship with number of already bundled Root CAs.
The intermediate CA certificate is issued by Root CA which means that Root CA private key is used to sign the intermediate certificate. The intermediate certificate then issue certificates to end entities. The end entities could be human, applications, servers or devices etc.
The intermediate CA issues certificates to end entities for different purposes. Some of the purposes are document signing certificates, SSL certificates, S/MIME and code signing etc.
Bridge PKI
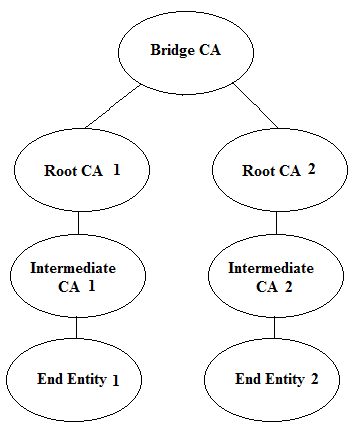
In this model, two hierarchical PKIs are connected using the Bridge CA. The Root CA 1 and Bridge CA are connected by issuing cross certificates to each other. In the same way Root CA 2 and Bridge CA are connected.
The applications that process the certificates from any of the two PKIs has to trust only the Bridge CA certificate. The trust will automatically be built by adding the Bridge CA in local trust anchor.
The certificate policies of both of these PKIs can also be mapped using the policy mapping certificate extension in the cross certificates.
The real example of bridge PKI is the US Federal Bridge CA.