PKCS#7 - SignedData
It is necessary to know how digital signatures are produced and verified, before moving on to PKCS#7 SignedData.
Signing and Verification
Following are the steps required for signature computation :
- Generate a public and private key pair using any of the key pair generation algorithm e.g. RSA
- Take the data on which signature needs to be computed
- Take the hash of the data using any of the hashing algorithm e.g. SHA256 etc
- Encrypt the hash with the private key. The output of the encryption of hash with the private key is the signature value
In order to verify the signature, following steps are required :
- In order to verify the signature, one should know the data that was signed, signature, hash algorithm and the public key
- Take the hash of the data using the same hashing algorithm that was used during signature computation i.e. SHA256
- Decrypt the signature with the public key. It will give you the hash
- Now compare both the hashes produced in above 2 steps. If both are equal then it means data is not tampered or you can say that the signature is verified otherwise data is tampered
Normally, one party is the signer and other is the verifier. If you have noticed the first step in the signature verification procedure. There should be some standard way of delivering all this information to the party that verifies the signature. PKCS#7 SignedData is one of the format to bundle all this information. There are other formats available i.e. PDF signatures, XML signatures and so on but in all these formats, the underlying cryptographic procedure for producing and verifying the signature is the same.
SignedData
PKCS#7 SignedData is a standard format for producing digital signature on any type of data. One can use this format when the data to be signed does not have the native digital signature capability in its format specification e.g. If you want to sign a text file, as it does not have the native signature capability in its format, so PKCS#7 SignedData can be used. If you want to sign PDF documents, as PDF documents have the native signature capability in its specification so these can be signed using the PDF signature specification. Also Microsoft Office documents have the native signature capability. You can also say that PKCS#7 SignedData can be used to produce signature on raw data.
In PKCS#7 SignedData, attached and detached formats are supported. In attached format, data that is signed is part of the SignedData package. For verification of the signature, application is not required to get the data as it is already embedded inside the SignedData. In detached format, data that is signed is not embedded inside the SignedData package instead it is placed at some external location. For verification of the signature, application is required to get the data from the external location and then verify the signature.
There are two types of signatures supported by PKCS#7 SignedData :
- Independent Signatures
- Counter Signatures
In independent signatures, all the signers sign the same data whereas in counter signatures, one signer signs the data and the next signer signs the signature of the previous signer and so on.
Structure
The structure of the PKCS#7 SignedData in ASN.1 format is shown below. You must be capable of reading the ASN.1 in order to fully understand the below PKCS#7 SignedData structure.
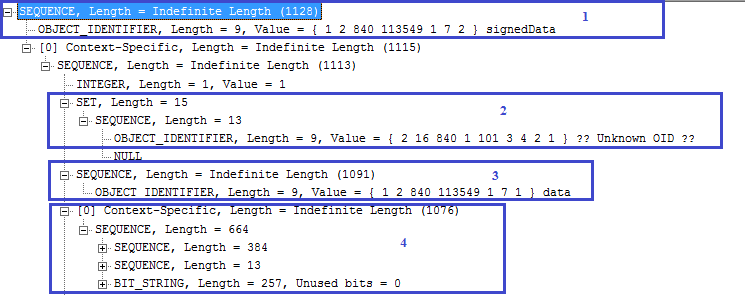
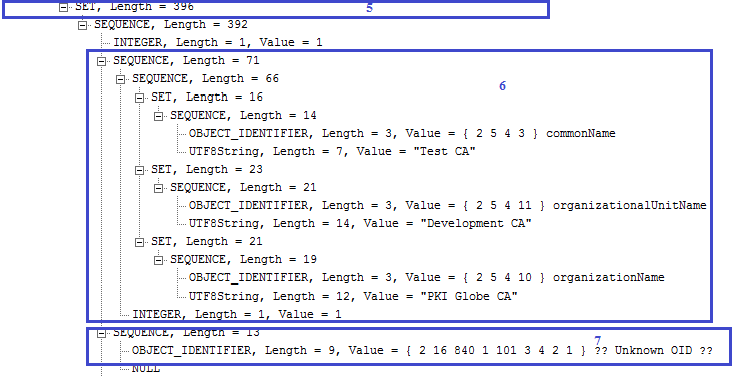
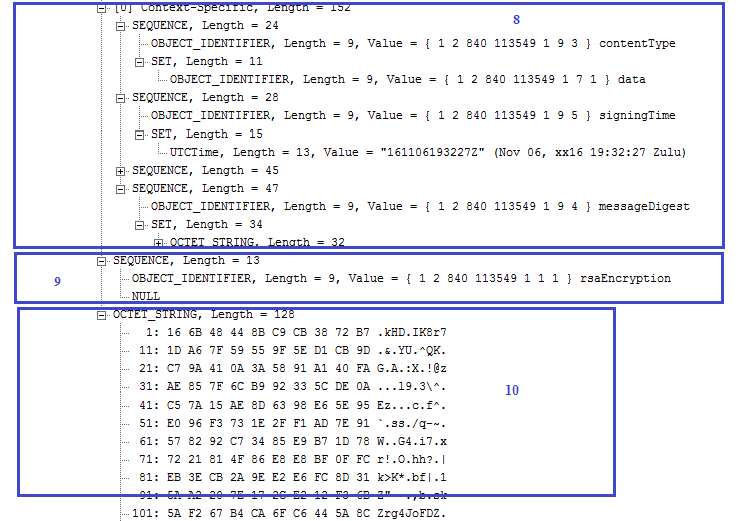
1) specifies the SignedData structure. 2) specifies the hashing algorithm used to produce the signature. The OID 2.16.840.1.101.3.4.2.1 shows that SHA256 hashing algorithm is used.3) specifies the detached format because no content is present. If it is in attached format then the content should be present here. 4) contains the signature certificate whose public key would be used to verify the signature. It can also contain complete signer certificate chain. 5) specifies the signerInfos structure. In case of independent signature, it should contain multiple signers information. 6) specifies the issuer and serial number structure. This structure helps in finding the signer certificate from the certificates list shown in 4). 7) specifies the hashing algorithm used to produce the signature. This should be same as mentioned in 2). 8) shows the authenticated attributes information. These attributes are part of signature computation. If any of the value of the authenticated attribute is changed then signature would not be verified. There are also unauthenticated attributes and if there is any change of value here then signature would still be verified. The unauthenticated attributes are not shown in this ASN.1 structure. 9) specifies the encryption algorithm and 10) specifies the signature value.
The above PKCS#7 structure is generated using the BouncyCastle library.