Authority Information Access (AIA) Extension
The Authority Information Access (AIA) is an X.509 v3 certificate extension. It contains at most two types of information :
- Information about how to get the issuer of this certificate (CA issuer access method)
- Address of the OCSP responder from where revocation of this certificate can be checked (OCSP access method)

In the above certificate, AIA extension is selected. The URL in the extension is pointing to the location where issuer of this certificate is located. When the client application downloads the issuer certificate from this location, it then again tries to look at the AIA extension of the downloaded certificate and tries to find the issuer of the downloaded certificate using the AIA extension. This process continues until reached to the trust anchor.
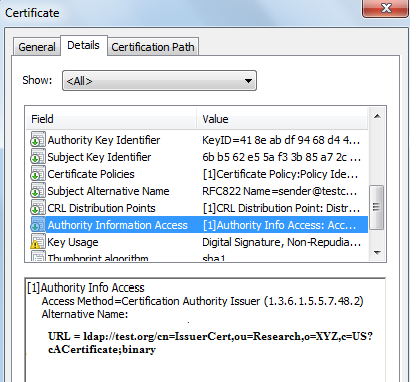
In the above certificate, the issuer of the certificate can be downloaded from the LDAP sever.
It is also possible to have two access locations in this extension, one pointing to the HTTP location while other pointing to LDAP location. In this case, both locations HTTP and LDAP would be pointing to the same issuer certificate.
In the above LDAP URL, ldap://test.org specifies the protocol name and the host while cn=IssuerCert,ou=Research,o=XYZ,c=US specifies the DN or the LDAP directory entry. The cACertificate;binary is the attribute in the LDAP directory entry where the issuer certificate is placed.
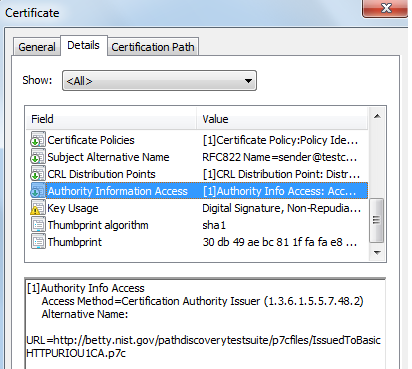
In the above certificate, the URL is pointing to a p7c which is a PKCS#7 certs list only file. It contains a list of certificates which includes the issuer certificate and all the cross certificates issued to the issuer of this certificate. The cross certificates are normally used in bridge PKI when the mutual trust is built using some bridge CA.
The general guess is, if the AIA URL is pointing to a certificate (.cer) file then it means the hierarchical PKI is used and if the AIA URL is pointing to a p7c file then it is assumed that bridge PKI is used i.e. two hierarchical PKIs can be connected using a bridge CA (Omitting the usage of Mesh PKI)
Applications use AIA certificate issuer access method to discover certificate paths using bottom up approach up to the trust anchor.
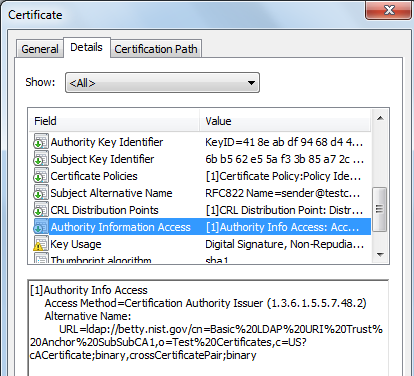
In the above certificate, the LDAP URL, ldap://betty.nist.gov specifies the protocol name and the host while cn=Basic%20LDAP%20URI%20Trust%20Anchor%20SubSubCA1,o=Test%20Certificates,c=US specifies the DN or the LDAP directory entry. The cACertificate;binary is the attribute in the LDAP directory entry where the issuer certificate is placed. The crossCerttificatePair;binary is also an attribute in the LDAP directory entry which contain cross certificates issued to this CA and issued by this CA.
If the issuer of this certificate is cross certified with multiple CAs then there will be a separate attribute entry of crossCertificatePair for each cross certified CA on LDAP server.
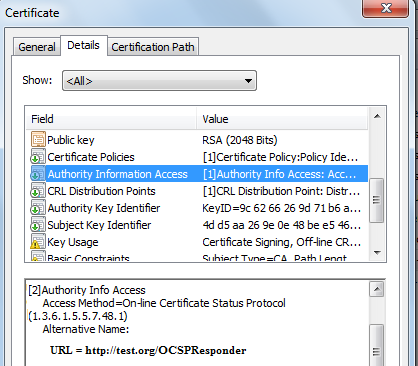
In the above certificate, the AIA extension access method is OCSP and the URL is the address of the OCSP responder from which the revocation of this certificate can be checked.