CRL Distribution Points (CDP) Extension
The CRL distribution points is an X.509 v3 certificate extension which identifies the location of the CRL from which the revocation of this certificate can be checked.
The application that processes the certificate can get the location of the CRL from this extension, download the CRL and then check the revocation of this certificate.
There are different ways in the CRL distribution points extension to describe the location of the CRL. Lets start with the CRL HTTP distribution point.
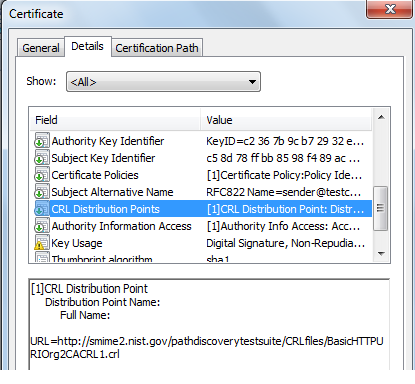
In the above certificate, the CRL distribution points extension is selected and points to the HTTP location of the CRL.
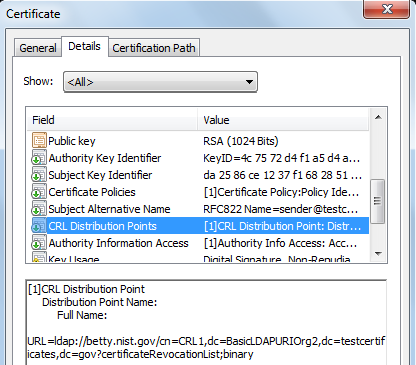
In the above certificate, the distribution point is pointing to the CRL location on the LDAP server.
It is also possible to have two distribution points in this extension, one pointing to the HTTP CRL location while other pointing to the LDAP CRL location. In this case, both distribution points HTTP and LDAP would be pointing to the same CRL.
In the above LDAP URL, ldap://betty.nist.gov specifies the protocol name and the host while cn=CRL1,dc=BasicLDAPURIOrg2,dc=testcertificates,dc=gov specifies the DN or the LDAP directory entry. The certificateRevocationList;binary is the attribute on the LDAP directory entry where the CRL for this certificate is placed.
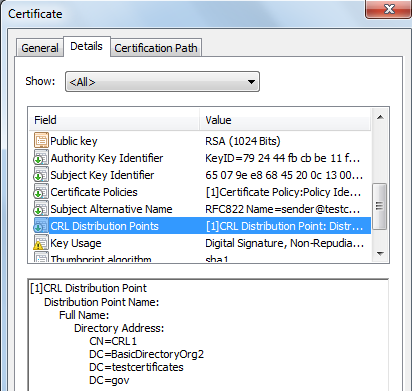
In the above certificate, the distribution point specifies the DN on the LDAP server. The host name for the LDAP server is not mentioned here. The host name will be configured at the application level. The application that processes this certificate takes the host name from the local configuration and the DN from this distribution point thus forms a complete LDAP URL where the CRL could be downloaded. Suppose the host name for the ldap is test.org then the complete LDAP URL would be ldap://test.org/CN=CRL1,DC=BasicDirectoryOrg2,DC=testcertificates,DC=gov?certificateRevocationList;binary.
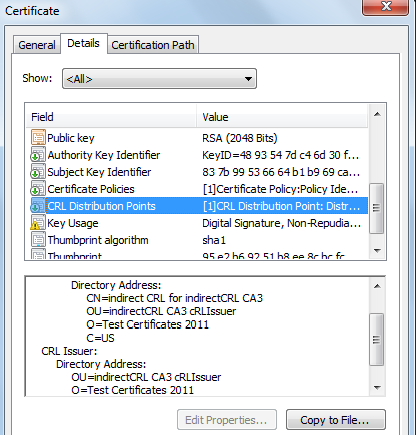
In the above certificate, the distribution point contains the DN where the CRL is located on the LDAP server while the CRL Issuer specifies that the downloaded CRL would be an indirect CRL. The DN under the CRL issuer specifies the location from where application can download the CRL issuer certificate in order to verify the CRL signature.
The LDAP URL for distribution point DN would be ldap://test.org/CN=indirect CRL for indirectCRL CA3,OU=indirectCRL CA3 cRLIssuer,O=Test Certificates 2011,C=US?certificateRevocationList;binary.
The LDAP URL for CRL issuer DN would be ldap://test.org/OU=indirectCRL CA3 cRLIssuer,O=Test Certificates 2011,C=US?userCertificate;binary. The output from this URL would be a CRL issuer certificate.
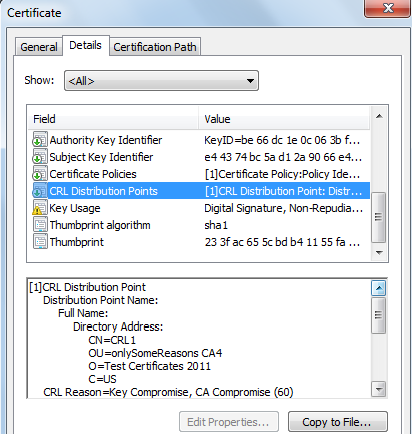
In the above certificate, the CRL is located at the specified DN on the LDAP server but this CRL only covers the certificates that are revoked with the Key Compromise and CA compromise reason codes. There would be separate CRL(s) for other reason codes. It is the responsibility of the application to download all the CRLs covering all of the reason codes defined in RFC 5280 and then check the revocation of the certificate in each of these CRLs because certificate can be revoked with any of the reason code.
There is another distribution point i.e. nameRelativeToCRLIssuer which describes a fragment of the DN. The fragment is appended with the CRL issuer to make a complete DN on the LDAP server. This complete DN would then be used to download the CRL from the LDAP server.