Name Constraints Extension
The name constraints extension is used in CA certificates. It specifies the constraints that apply on subject distinguished names and subject alternative names of subsequent certificates in the certificate path.
These constraints can be applied in the form of permitted or excluded names. If a constraint is mentioned in the permitted names list, then the subsequent certificates must comply with this constraint. If the constraint is mentioned in the excluded names list, then satisfying the constraint results in failure of path validation.
The following constraints can majorly be applied:
- Directory Name
- DNS
- Email address
- URIs
- IP address
In order to make things simple, I will use the issuing CA and an end entity certificate in all of my below examples.
Directory Name
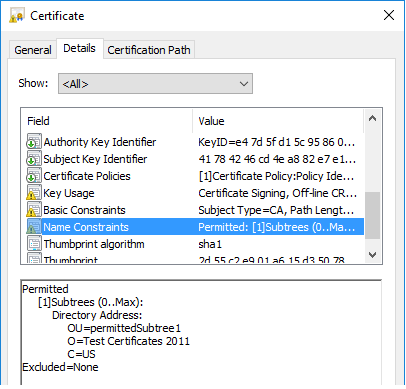
In the above CA certificate, the name constraints extension is present. It specifies a constraint on the subject DN of the subsequent end entity certificate and is also in the permitted names list. There are no restrictions applied on the excluded names list.
In the below end entity certificate, the subject DN OU, O and C values are according to the constraint and are also in the same order. The below end entity certificate complies with the name constraints extension.
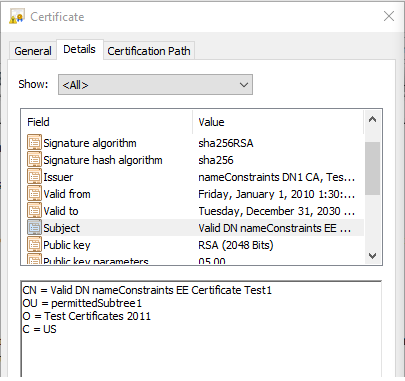
If the subject DN in the above end entity certificate changes to:
CN = Invalid DN nameConstraints EE Certificate Test2 OU = excludedSubtree1 O = Test Certificates 2011 C = US
Then it does not comply with the constraint because of the change of OU value in the subject DN.
DNS
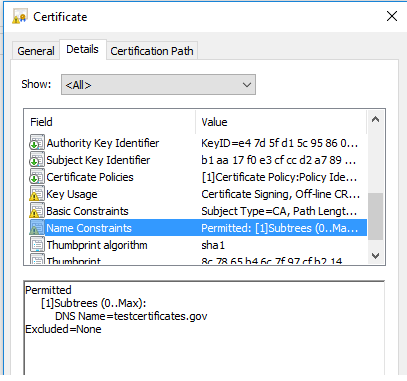
In the above CA certificate, the name constraints extension is applied on DNS name. The DNS name in the subject alternative name extension of the subsequent end entity certificate must comply with this constraint.
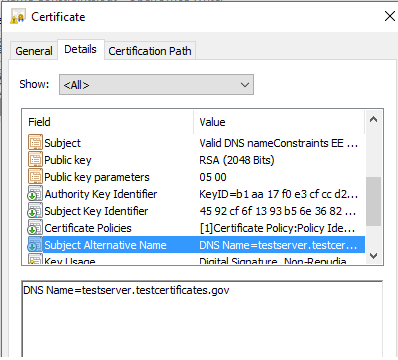
The testserver.testcertificates.gov subdomain complies with the domain testcertificates.gov in the name constraints extension. The testcertificates.gov in the subject alternative name of an end entity certificate would also comply with this constraint.
Email address
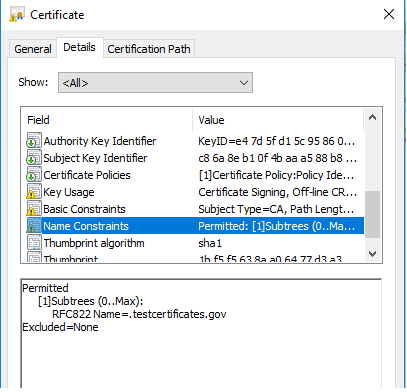
In the above CA certificate, the name constraints extension is applied on email addresses in the subsequent end entity certificate. The dot operator specifies all mail boxes in a domain e.g. Test21EE@mailserver.testcertificates.gov is a legal value in the subject alternative name in the subsequent end entity certificate as shown below.
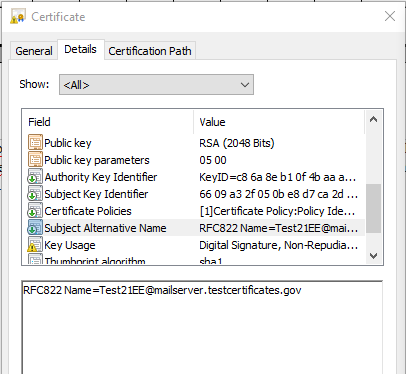
If the value in the above certificate changes to Test21EE@xyz.testcertificates.gov then it also complies with the name constraints extension because of the dot operator.
If the name constraints extension value changes to testcertificates.gov then Test21EE@testcertificates.gov and xyz@testcertificates.gov are all legal values in the SAN of subsequent end entity certificate. It covers all the email addresses under testcertificates.gov host.
One can also specify an email address in the name constraints extension. In this case, only that particular email address is acceptable in the SAN of subsequent end entity certificate.
Note:- The URIs and IP address constraints are not covered.